Ten papers by CSE researchers at USENIX Security 2024

Ten papers by CSE authors have been accepted for presentation at the 2024 USENIX Security Symposium, one of the leading international conferences in the field of computer security. Taking place August 14-16, 2024, in Philadelphia, the symposium brings together researchers and practitioners from around the world to discuss and share the latest findings related to computer and network security and privacy.
The papers being presented by CSE researchers cover a range of topics in this field, including data fabrication attacks in autonomous vehicle networks, proxy detection using encapsulated TLS handshakes, a novel technique for combating rowhammer attacks, and more. Two of the CSE papers presented received distinguished paper awards.
The following papers were presented at the conference, with the names of CSE researchers in bold:
DVSorder: Ballot Randomization Flaws Threaten Voter Privacy
Braden L. Crimmins, Dhanya Y. Narayanan, Drew Springall, J. Alex Halderman
Distinguished Paper Award Winner
Abstract: A trend towards publishing ballot-by-ballot election results has created new risks to voter privacy due to inadequate protections by election technology. These risks are manifested by a vulnerability we discovered in precinct-based ballot scanners made by Dominion Voting Systems, which are used in parts of 21 states and Canada. In a variety of scenarios, the flaw—which we call DVSorder—would allow attackers to link individuals with their votes and compromise ballot secrecy. The root cause is that the scanners assign pseudorandom ballot identifiers using a linear congruential generator, an approach known since the 1970s to be insecure. Dominion attempted to obfuscate the generator’s output, but we show that it can be broken using only pen and paper to reveal the order in which all ballots were cast. Unlike past ballot randomization flaws, which typically required insider access to exploit or access to proprietary software to discover, DVSorder can be discovered and exploited using only public information.
In addition, the election sector’s response to our findings provides a case study highlighting gaps in regulations and vulnerability management within this area of critical infrastructure. Although Dominion released a software update in response to DVSorder, some localities have continued to publish vulnerable data due to inadequate information sharing and mitigation planning, and at least one state has deferred addressing the flaw until after the 2024 presidential election, more than two years following our disclosure.
Digital Discrimination of Users in Sanctioned States: The Case of the Cuba Embargo
Anna Ablove, Shreyas Chandrashekaran, Hieu Le, Ram Sundara Raman, Reethika Ramesh, Harry Oppenheimer, Roya Ensafi
Distinguished Paper Award Winner
Abstract: We present one of the first in-depth and systematic end-user centered investigations into the effects of sanctions on geoblocking, specifically in the case of Cuba. We conduct network measurements on the Tranco Top 10K domains and complement our findings with a small-scale user study with a questionnaire. We identify 546 domains subject to geoblocking across all layers of the network stack, ranging from DNS failures to HTTP(S) response pages with a variety of status codes. Through this work, we discover a lack of user-facing transparency; we find 88% of geoblocked domains do not serve informative notice of why they are blocked. Further, we highlight a lack of measurement-level transparency, even among HTTP(S) blockpage responses. Notably, we identify 32 instances of blockpage responses served with 200 OK status codes, despite not returning the requested content. Finally, we note the inefficacy of current improvement strategies and make recommendations to both service providers and policymakers to reduce Internet fragmentation.
Go Go Gadget Hammer: Flipping Nested Pointers for Arbitrary Data Leakage
Youssef Tobah, Andrew Kwong, Ingab Kang, Daniel Genkin, Kang G. Shin
Abstract: Rowhammer is an increasingly threatening vulnerability that grants an attacker the ability to flip bits in memory without directly accessing them. Despite efforts to mitigate Rowhammer via software and defenses built directly into DRAM modules, more recent generations of DRAM are actually more susceptible to malicious bit-flips than their predecessors. This phenomenon has spawned numerous exploits, showing how Rowhammer acts as the basis for various vulnerabilities that target sensitive structures, such as Page Table Entries (PTEs) or opcodes, to grant control over a victim machine.
However, in this paper, we consider Rowhammer as a more general vulnerability, presenting a novel exploit vector for Rowhammer that targets particular code patterns. We show that if victim code is designed to return benign data to an unprivileged user, and uses nested pointer dereferences, Rowhammer can flip these pointers to gain arbitrary read access in the victim’s address space. Furthermore, we identify gadgets present in the Linux kernel, and demonstrate an end-to-end attack that precisely flips a targeted pointer. To do so we developed a number of improved Rowhammer primitives, including kernel memory massaging, Rowhammer synchronization, and testing for kernel flips, which may be of broader interest to the Rowhammer community. Compared to prior works’ leakage rate of .3 bits/s, we show that such gadgets can be used to read out kernel data at a rate of 82.6 bits/s.
By targeting code gadgets, this work expands the scope and attack surface exposed by Rowhammer. It is no longer sufficient for software defenses to selectively pad previously exploited memory structures in flip-safe memory, as any victim code that follows the pattern in question must be protected.
On Data Fabrication in Collaborative Vehicular Perception: Attacks and Countermeasures
Qingzhao Zhang, Shuowei Jin, Ruiyang Zhu, Jiachen Sun, Xumiao Zhang, Qi Alfred Chen, Z. Morley Mao
Abstract: Collaborative perception, which greatly enhances the sensing capability of connected and autonomous vehicles (CAVs) by incorporating data from external resources, also brings forth potential security risks. CAVs’ driving decisions rely on remote untrusted data, making them susceptible to attacks carried out by malicious participants in the collaborative perception system. However, security analysis and countermeasures for such threats are absent. To understand the impact of the vulnerability, we break the ground by proposing various real-time data fabrication attacks in which the attacker delivers crafted malicious data to victims in order to perturb their perception results, leading to hard brakes or increased collision risks. Our attacks demonstrate a high success rate of over 86% on high-fidelity simulated scenarios and are realizable in real-world experiments. To mitigate the vulnerability, we present a systematic anomaly detection approach that enables benign vehicles to jointly reveal malicious fabrication. It detects 91.5% of attacks with a false positive rate of 3% in simulated scenarios and significantly mitigates attack impacts in real-world scenarios.

CalcuLatency: Leveraging Cross-Layer Network Latency Measurements to Detect Proxy-Enabled Abuse
Reethika Ramesh, Philipp Winter, Sam Korman, Roya Ensafi
Abstract: Efforts from emerging technology companies aim to democratize the ad delivery ecosystem and build systems that are privacy-centric and even share ad revenue benefits with their users. Other providers offer remuneration for users on their platform for interacting with and making use of services. But these efforts may suffer from coordinated abuse efforts aiming to defraud them. Attackers can use VPNs and proxies to fabricate their geolocation and earn disproportionate rewards. Balancing proxy-enabled abuse-prevention techniques with a privacy-focused business model is a hard challenge. Can service providers use minimal connection features to infer proxy use without jeopardizing user privacy?
In this paper, we build and evaluate a solution, CalcuLatency, that incorporates various network latency measurement techniques and leverage the application-layer and network-layer differences in roundtrip-times when a user connects to the service using a proxy. We evaluate our four measurement techniques individually, and as an integrated system using a two-pronged evaluation. CalcuLatency is an easy-to-deploy, open-source solution that can serve as an inexpensive first-step to label proxies.
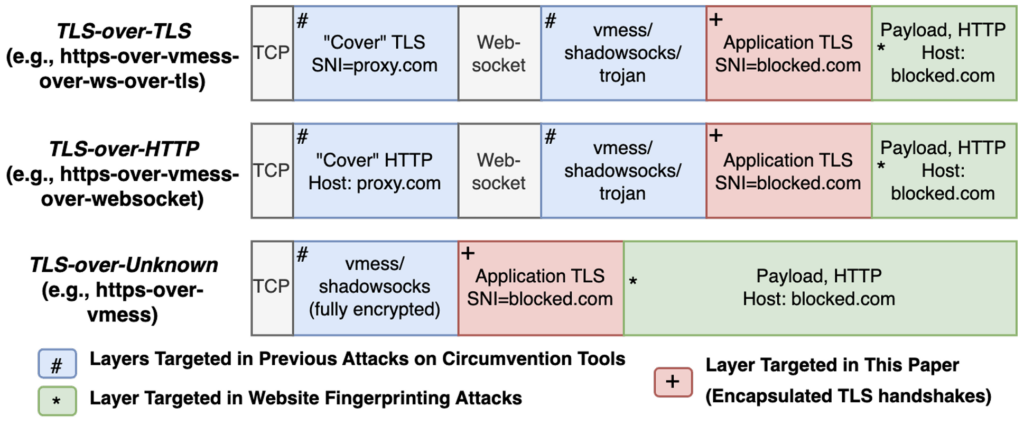
Fingerprinting Obfuscated Proxy Traffic with Encapsulated TLS Handshakes
Diwen Xue, Michalis Kallitsis, Amir Houmansadr, Roya Ensafi
Abstract: The global escalation of Internet censorship by nation-state actors has led to an ongoing arms race between censors and obfuscated circumvention proxies. Research over the past decade has extensively examined various fingerprinting attacks against individual proxy protocols and their respective countermeasures. In this paper, however, we demonstrate the feasibility of a protocol-agnostic approach to proxy detection, enabled by the shared characteristic of nested protocol stacks inherent to all forms of proxying and tunneling activities. We showcase the practicality of such approach by identifying one specific fingerprint–encapsulated TLS handshakes–that results from nested protocol stacks, and building similarity-based classifiers to isolate this unique fingerprint within encrypted traffic streams.
Assuming the role of a censor, we build a detection framework and deploy it within a mid-size ISP serving upwards of one million users. Our evaluation demonstrates that the traffic of obfuscated proxies, even with random padding and multiple layers of encapsulations, can be reliably detected with minimal collateral damage by fingerprinting encapsulated TLS handshakes. While stream multiplexing shows promise as a viable countermeasure, we caution that existing obfuscations based on multiplexing and random padding alone are inherently limited, due to their inability to reduce the size of traffic bursts or the number of round trips within a connection. Proxy developers should be aware of these limitations, anticipate the potential exploitation of encapsulated TLS handshakes by the censors, and equip their tools with proactive countermeasures.
Bridging Barriers: A Survey of Challenges and Priorities in the Censorship Circumvention Landscape
Diwen Xue, Anna Ablove, Reethika Ramesh, Grace Kwak Danciu, Roya Ensafi
Abstract: The ecosystem of censorship circumvention tools (CTs) remains one of the most opaque and least understood, overshadowed by the precarious legal status around their usage and operation, and the risks facing those directly involved. Used by hundreds of millions of users across the most restricted networks, these tools circulate not through advertisements but word-of-mouth, distributed not through appstores but underground networks, and adopted not out of trust but from the sheer necessity for information access.
This paper aims to elucidate the dynamics and challenges of the CT ecosystem, and the needs and priorities of its stakeholders. We perform the first multi-perspective study, surveying 12 leading CT providers that service upwards of 100 million users, combined with experiences from CT users in Russia and China. Beyond the commonly cited technical challenges and disruptions from censors, our study also highlights funding constraints, usability issues, misconceptions, and misbehaving players, all of which similarly plague the CT ecosystem. Having the unique opportunity to survey these at-risk CT stakeholders, we outline key future priorities for those involved. We hope our work encourages further research to advance our understanding of this complex and uniquely challenged ecosystem.
SpotProxy: Rediscovering the Cloud for Censorship Circumvention
Patrick Tser Jern Kon, Sina Kamali, Jinyu Pei, Diogo Barradas, Ang Chen, Micah Sherr, Moti Yung
Abstract: Censorship circumvention is often fueled by supporters out of goodwill. However, hosting circumvention proxies can be costly, especially when they are placed in the cloud. We argue for re-examining cloud features and leveraging them to achieve novel circumvention benefits, even though these features are not explicitly engineered for censorship circumvention. SpotProxy is inspired by Spot VMs—cloud instances backed with excess resources, sold at a fraction of the cost of regular instances, that can be taken away at a moment’s notice if higher-paying requests arrive. We observe that for circumvention proxies, Spot VMs not only translate to cost savings, but also create a high churn rate since proxies are constantly re-spawned at different IP addresses—making them more difficult for a censor to enumerate and block. SpotProxy pushes this observation to the extreme and designs a circumvention infrastructure that constantly searches for cheaper VMs and refreshes the fleet for anti-blocking, for spot and regular VMs alike. We adapt Wireguard and Snowflake for use with SpotProxy, and demonstrate that our active migration mechanism allows clients to seamlessly move between proxies without degrading their performance or disrupting existing connections. We show that SpotProxy leads to significant cost savings, and that SpotProxy’s rejuvenation mechanism enables proxies to be replenished frequently with new addresses.
SledgeHammer: Amplifying Rowhammer via Bank-level Parallelism
Ingab Kang, Walter Wang, Jason Kim, Stephan van Schaik, Youssef Tobah, Daniel Genkin, Andrew Kwong, Yuval Yarom
Abstract: Rowhammer is a hardware vulnerability in DDR memory by which attackers can perform specific access patterns in their own memory to flip bits in adjacent, uncontrolled rows with- out accessing them. Since its discovery by Kim et. al. (ISCA 2014), Rowhammer attacks have emerged as an alarming threat to numerous security mechanisms.
In this paper, we show that Rowhammer attacks can in fact be more effective when combined with bank-level parallelism, a technique in which the attacker hammers multiple memory banks simultaneously. This allows us to increase the amount of Rowhammer-induced flips 7-fold and significantly speed up prior Rowhammer attacks relying on native code execution.
Furthermore, we tackle the task of mounting browser-based Rowhammer attacks. Here, we develop a self-evicting version of multi-bank hammering, allowing us to replace clflush instructions with cache evictions. We then develop a novel method for detecting contiguous physical addresses using memory access timings, thereby obviating the need for trans- parent huge pages. Finally, by combining both techniques, we are the first, to our knowledge, to obtain Rowhammer bit flips on DDR4 memory from the Chrome and Firefox browsers running on default Linux configurations, without enabling transparent huge pages.
Lotto: Secure Participant Selection against Adversarial Servers in Federated Learning
Zhifeng Jiang, Peng Ye, Shiqi He, Wei Wang, Ruichuan Chen, Bo Li
Abstract: In Federated Learning (FL), common privacy-enhancing techniques, such as secure aggregation and distributed differential privacy, rely on the critical assumption of an honest majority among participants to withstand various attacks. In practice, however, servers are not always trusted, and an adversarial server can strategically select compromised clients to create a dishonest majority, thereby undermining the system’s security guarantees. In this paper, we present Lotto, an FL system that addresses this fundamental, yet underexplored issue by providing secure participant selection against an adversarial server. Lotto supports two selection algorithms: random and informed. To ensure random selection without a trusted server, Lotto enables each client to autonomously determine their participation using verifiable randomness. For informed selection, which is more vulnerable to manipulation, Lotto approximates the algorithm by employing random selection within a refined client pool. Our theoretical analysis shows that Lotto effectively aligns the proportion of server-selected compromised participants with the base rate of dishonest clients in the population. Large-scale experiments further reveal that Lotto achieves time-to-accuracy performance comparable to that of insecure selection methods, indicating a low computational overhead for secure selection.
 MENU
MENU 
